Privacy and security have long-been one of the top selling points for iOS devices in the interminable marketing fracas between Apple and its competitors, with fancy additions to their suite of protection features like fingerprint scanning and facial recognition. Android devices, by contrast, always seemed to lag behind in the personal encryption space, but have caught up fairly recently in the consumer’s mind, at least.
The cat, as they say, is out of the bag thanks to researchers at Johns Hopkins University, who decided to test the mobile security systems of two of the biggest mobile device makers, Apple and Google. Their findings reveal that the layers of security protecting our data are only skin deep and that much of the encryption structures built into these devices remain unused. “I’ve come out of the project thinking almost nothing is protected,” Matthew Green, the professor who oversaw the study told Wired.
Using the companies’ own data and records spanning over a decade, the team of cryptographers found a plethora of security loopholes that can and are being exploited “by hackers and law enforcement alike.” The latter’s access to our mobile devices is of particular concern, given “the privacy risks involved in unchecked seizure and search.” Significantly, it is not your local police precinct that necessarily has the right tools to extract any readable data from your cell phone or laptop (though that is changing), but rather, these unique abilities are reserved for private cybersecurity companies who offer their services to police and other government entities.
One such firm, Israeli cyber forensics firm Cellebrite, boasts about their ability to “unlock and extract data from all iOS and high-end Android devices,” a service they have been selling to governments around the world and which they have more recently integrated into a product called Universal Forensic Extraction Device or UFED, which has been purchased by multiple law enforcement agencies across the globe, including the Hong Kong Police, which used Cellebrite’s hacking technology to “crack protestors’ smartphones” during the anti-extradition riots of 2019 and the NYPD, which enrolled in Cellebrite’s “UFED Premium program” that same year and gives ‘New York’s finest’ the capability to extract ostensibly private citizens’ data from the department’s own computers and laptops.
Cellebrite’s Celebrity
Acquired by a relatively obscure Japanese video game developer, Sun Corporation (Sunsoft) in 2007, Cellebrite started to seep into the public eye as a result of the San Bernardino mass shooting of 2015 when Syed Rizwan Farook along with his wife and son opened fire inside the San Bernardino County seat during a public health event, leaving 14 dead.
Farook and his accomplices were among the first to be described by U.S. law enforcement as “homegrown violent extremists” who had been influenced by foreign terrorist groups and radicalized on the Internet, presaging the current trend in American political discourse in the wake of the Capitol riots and the justification for the creation of domestic terrorist laws and mass deplatforming actions by big tech.
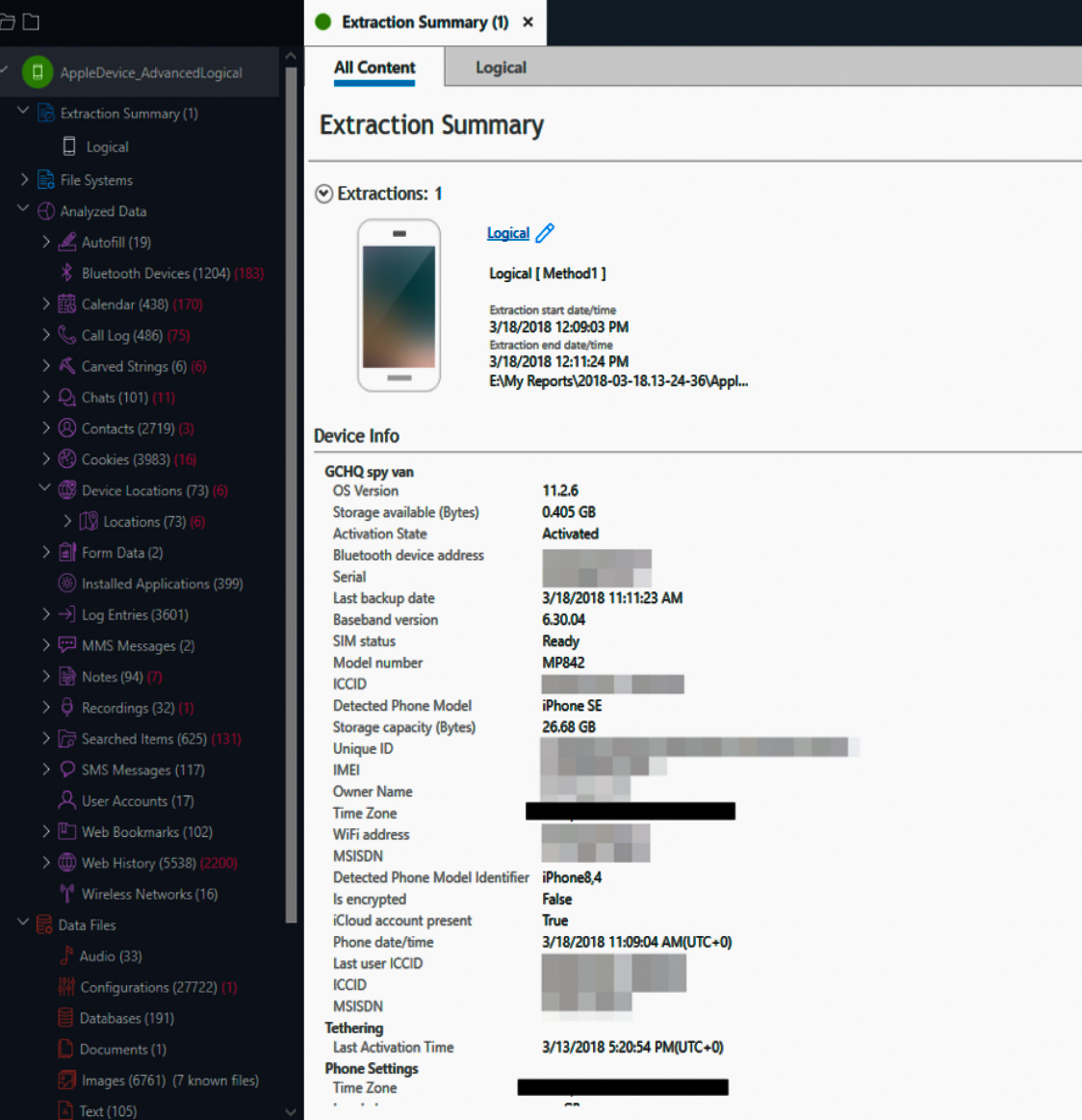
The incident also spawned a highly-publicized dispute between the FBI and Apple over law enforcement agencies’ right to compel device manufacturers to unlock cell phones’ data encryption features in order to assist in criminal investigations. The controversy between the FBI and the Silicon Valley behemoth escalated as Apple successfully resisted the attempts to break its promises of privacy to its customers in court. In the meantime, Cellebrite came along and offered to bypass Apple’s vaunted encryption for the FBI, which they did easily, according to Cellebrite CEO, Yossi Carmil.
By 2019, Cellebrite was said to control half of the global digital forensics market, according to the Ynet article, in which Carmil brags that the company counts with “specialized iOS and Android capabilities that no one else has anywhere in the world.”
Fair Comparisons
Despite the apparent conflict Cellebrite has with Apple and other mobile device manufacturers, Carmil asserts that the iPhone-maker is “quite satisfied with the use of Cellebrite’s technology”, perhaps because the arrangement allows the world’s most profitable tech company to maintain the pretense of a robust privacy offering to its global customer base.
Cellebrite has drawn comparisons to another Israeli cyber hacking firm called NSO Group, which is known to deploy spyware and other surveillance tools on behalf of highly-suspect government entities and independent state actors. Pegasus spyware, one of NSO’s most notorious contributions to the dark world of cyberwarfare, has been found to be behind cyber attack operations in 45 countries, according to a study by Citizen Lab.

Among the scandals traced back to Pegasus spyware was its use in the targeting of dozens of Mexican journalists, lawyers, and advocates investigating the country’s drug cartels and the mass disappearance of 43 students from Ayotzinapa Rural Teachers College in 2014 – a case that implicates none other than the recently repatriated General Salvador Cienfuegos. NSO’s spyware has been linked to the assassination of at least one award-winning Mexican journalist who had founded a newspaper dedicated to investigating the nation’s drug cartels.
Carmil dismisses the similarities between NSO and Cellebrite, assuring us that he “sleeps well at night,” confident in the fact that his company is “on the good side.” Despite his resentment over what he considers an unfair association, Carmil “appreciates [the] know-how” of his industry colleagues at NSO, which he admits to knowing. He is unapologetic, however, about the true nature of his business and is proud to work with agencies like the U.S. Immigrations and Customs Enforcement (ICE) to capture people who end up in their detention facilities, where some are subjected to hysterectomies and other invasive surgical procedures against their will.
“The world is not innocent,” Carmil decrees. “When I need to take data from immigrants to keep my country safe, I feel I am on the right side of the law,” he continues. It is unclear what country, specifically, Carmil is referring to as Cellebrite operates in 150 countries around the world and has just finished signing a $3 million contract with an undisclosed government agency in Abu Dhabi in a deal brokered by former Mossad agent, David Meidan.
Meidan headed a special department for the Israeli spy agency in the United Arab Emirates (UAE) called Tevel, which functioned as an unofficial “foreign ministry,” tasked with managing “the secret ties between the Jewish state and the Arab and Muslim world” and which, naturally, dealt directly with Abu Dhabi’s Crown Prince and deputy commander of the UAE armed forces Sheikh Mohammed Bin Zayed, who is one of the best customers of NSO’s Pegasus spyware.
Feature photo | A man looks at his cellphone as he walks on the street in downtown Madrid. Francisco Seco. | AP
Raul Diego is a MintPress News Staff Writer, independent photojournalist, researcher, writer and documentary filmmaker.


